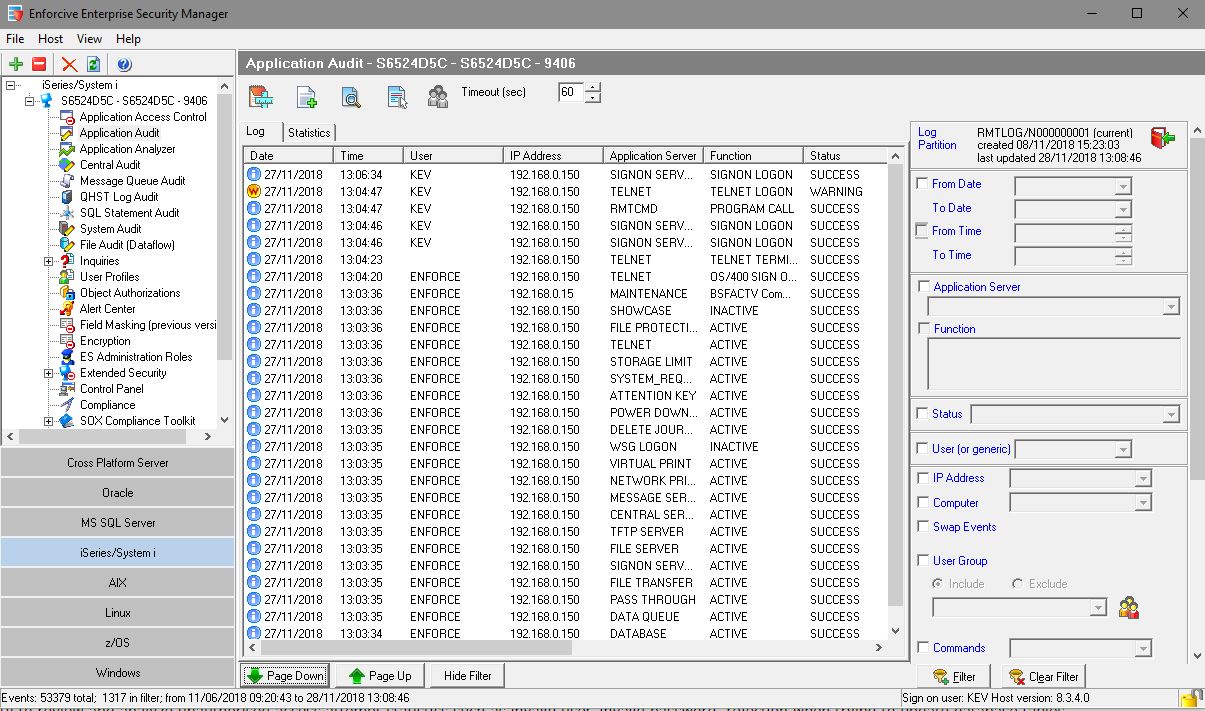
This is the audit log for application access activity(exit program controlled activity) to the IBM i Server
It allows quick and easy identification of access events and identifies trends
Architecture
- View of audit data via the desktop GUI
- Based on logs created by exit programs as dictated by the Application Access Control Definitions
Highlights
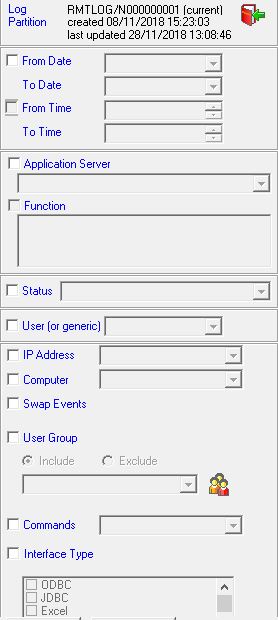
- Powerful filtering capability
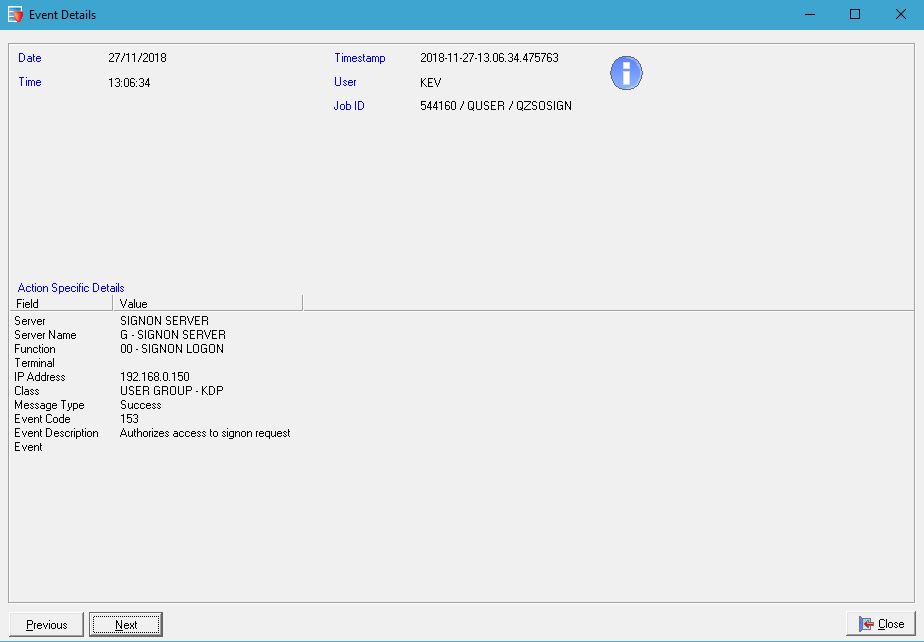
- Event level detail, includes Transaction ,user IP address and Object
- Graph and table display options
- Predefined summary and event reports
- User defined event reports
Organizational Benefits
- Ability to investigate security incidents at the level of server activity
- Ability to review and analyze application access trends such as security officer activity, specific library and file access, application usage types such as ODBC,FTP, remote command,database
- Ability to review and analyze unauthorised access attempt statistics such as invalid user, invalid password, rejection when trying to update database tables
- Provides an online log of activity that is not monitored by the operating system
- Answers information systems auditing compliance requirements