This module forms the base module and provides protection/auditing from unauthorized activity coming from the TCP/IP network, blocking intruders, malicious or errant users, thus reducing the chance of database corruption and unauthorized use or theft of data.
Architecture
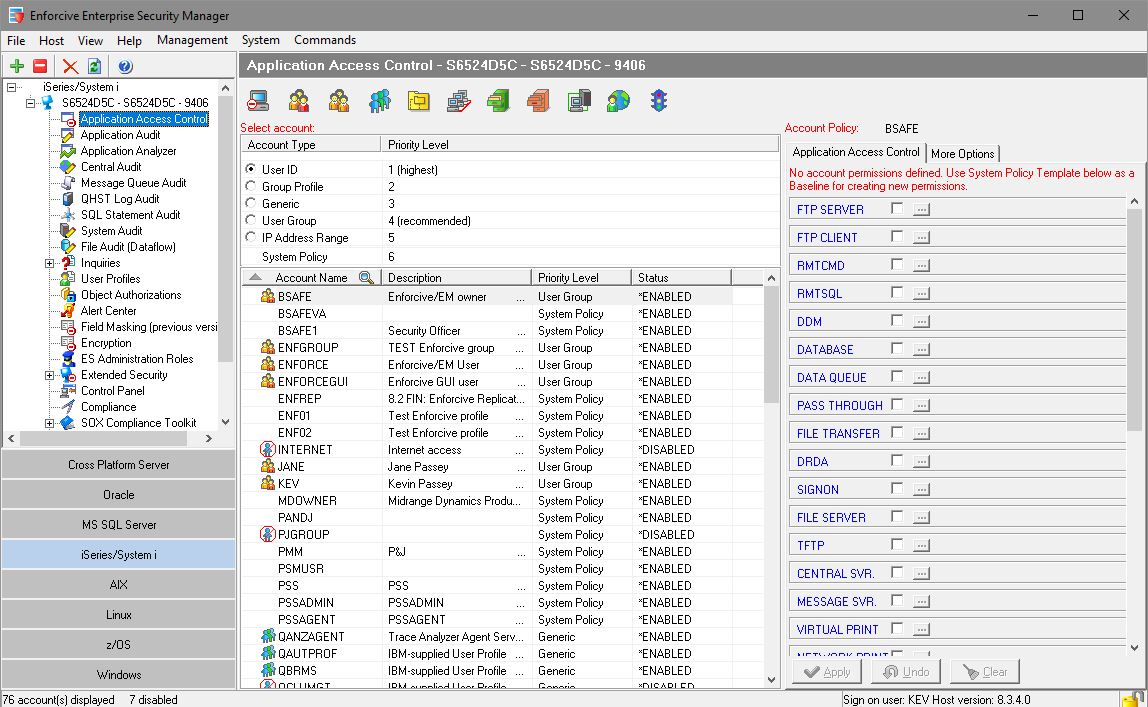
- Permissions definitions via the GUI based interface
- Server base exit point management using proprietary exit programs
Highlights
- Provides an additional layer of protection on top of the operating systems object security
- Role based management
- General system policy and additional custom user groups with special permissions according to role
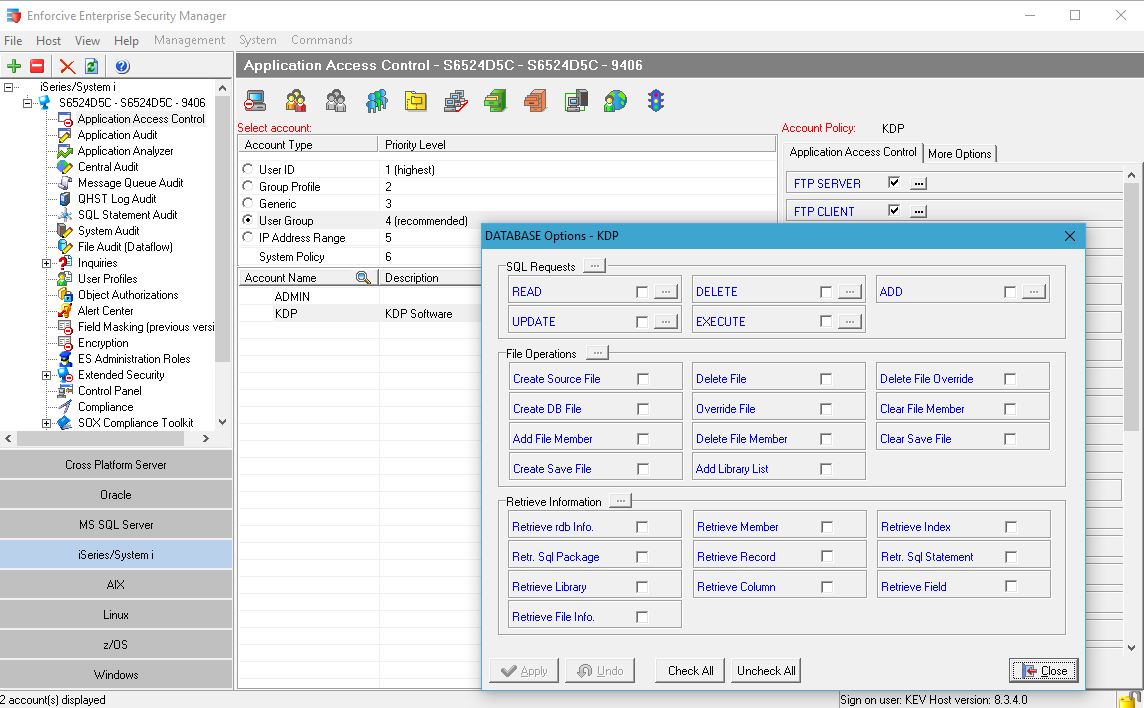
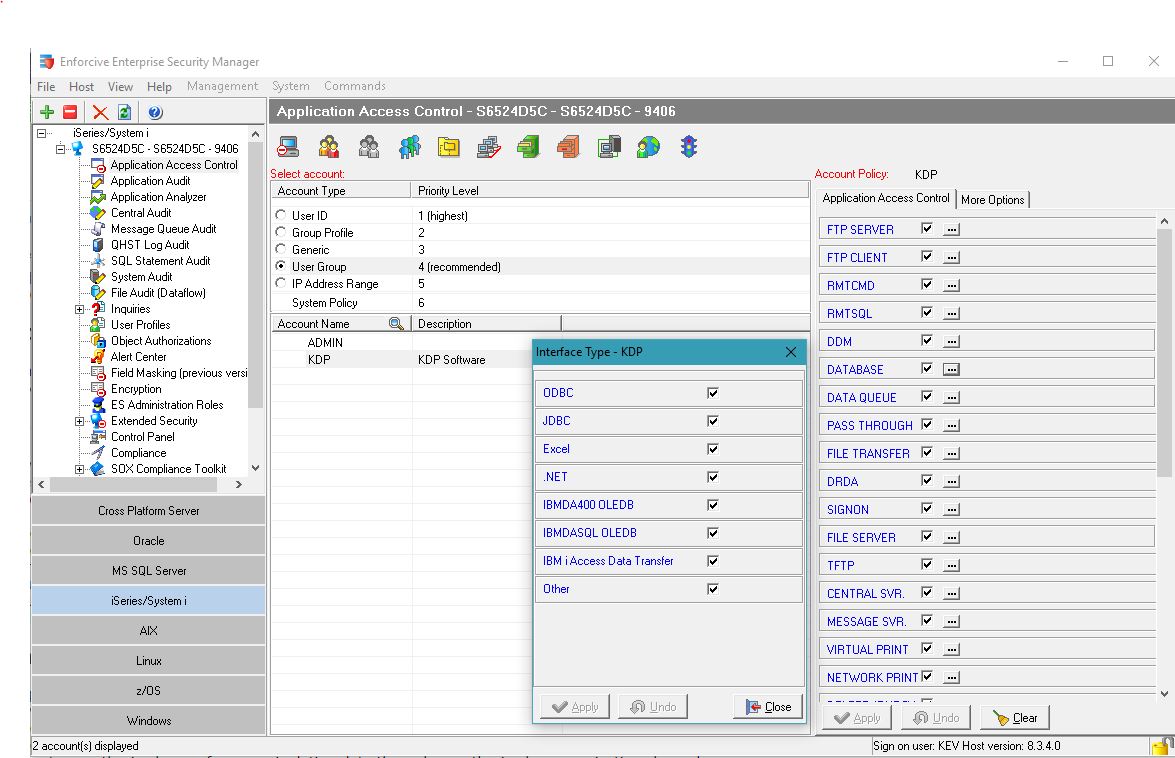
- Intuitive: Rapid roll out of granular permissions by user or group, exit point, function, library and object
- Protection of commands, these can be system commands or 3rd party written commands
- Protection of files (optional) by read, add, change, delete
- Authority swapping - a controlled way of granting elevated authority on a temporary basis
- Simulation mode for safe and phased implementation
- Regulation of exit point activity by IP address
- Replication of definitions across servers and/or LPARS
Organizational Benefits
- Supports roll based security
- Prevents power user authority misuse
- Protects against data theft, database manipulation
- Protects against object tampering
- Prevents unauthorized users from manipulating data through unauthorized communication channels
- Improves privacy, security and robustness of IBM i based applications and databases
- Facilitates regulatory compliance such as GDPR etc