IBMi - Auditing The Use Of QSECOFR
Some of these examples are built from the IBMi Security Administration and Compliance book and implemented in Enforcive installed on an IBMi.
Following on from my previous post Auditing Password Authorization Failures once you are auditing password use, the next step is to monitor important user profiles, we are using QSECOFR in this example but this can be applied to any profile.
Auditing The Use Of QSECOFR
Before setting up Alerts and reports on jobs, check that the System Audit Policy in Enforcive includes *JOBDTA and that the System Security Journal has been started on the Alert collector Panel.
If you want to do this manually you need to change the system value QAUDLVL to include *JOBDTA then we will use the JS action type (Actions that affect jobs).

Using Enforcive it's as easy as ticking the *JOBDTA element in the System audit policy.
Good Security Practice is not to use QSECOFR or any of the system provided "Q" profiles, you should give individual profiles the authority they need to perform the required actions even if it is on a temporary basis.
With that in mind it is also good practice to monitor the use of QSECOFR as this is a powerful profile on the IBMi - for many of our clients this is also an Audit requirement.
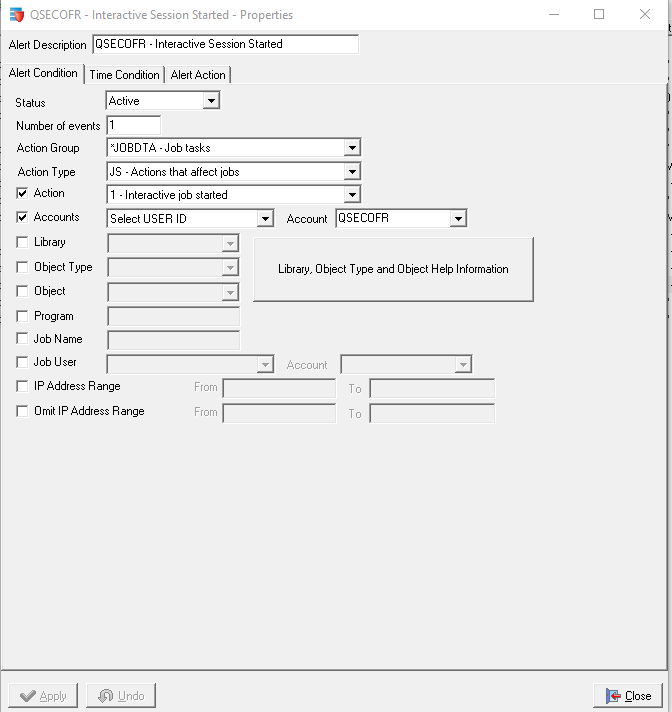
This is done using the JS action type and the relevant action codes. Using Enforcive's Alert center the user can monitor action type JS and action 1 which monitors for an interactive job started event.
The Alert Action is configured to send an email alert plus the alert is logged in Enforcive's central audit.

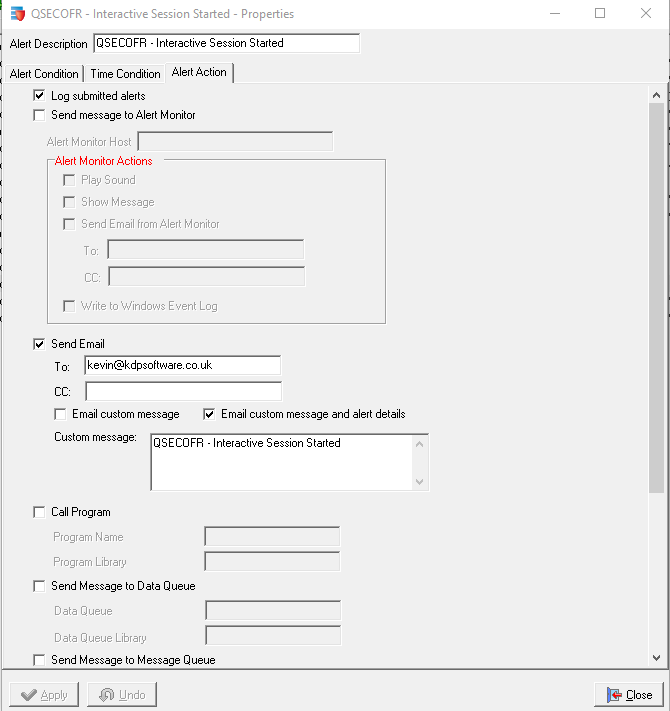
This is the resulting email
QSECOFR - Interactive Session Started ------ System:LS089;QSECOFR - Interactive Session Started DATE: 2023-01-23 TIME: 11:16:19 TYPE: JOB TASKS USER: QSECOFR DATA: JOB 086115/QSECOFR/KDPA1 JOB TYPE = INTERACTIVE STARTED EFFECTIVE USER = QSECOFR REAL USER = QSECOFR SAVED USER = QSECOFR FROM IP ADDRESS: xxx.xxx.xxx.xxx JOB ID: 086115/QSECOFR/KDPA1
So the first example shows when an Interactive Job is started using the QSECOFR profile.
Additional JS actions are as follows:-
- Action Type JS action 2 = Interactive Job Ended
- Action Type JS action B = Batch Job Submitted
- Action Type JS action S = A Job was started
- Action Type JS action H = A Job was held
- Action Type JS action E = A Job was ended
Using the *SECURITY tasks Action Group the following code can also be monitored and alerted on.
Action Type CP action A = A User Profile changed, created or restored
Enforcive can also determine if a profile is disabled, or the password changed, or even if the profile is disabled by the system following Invalid password attempts. If the latter is the case there are various actions Enforcive can perform - see below

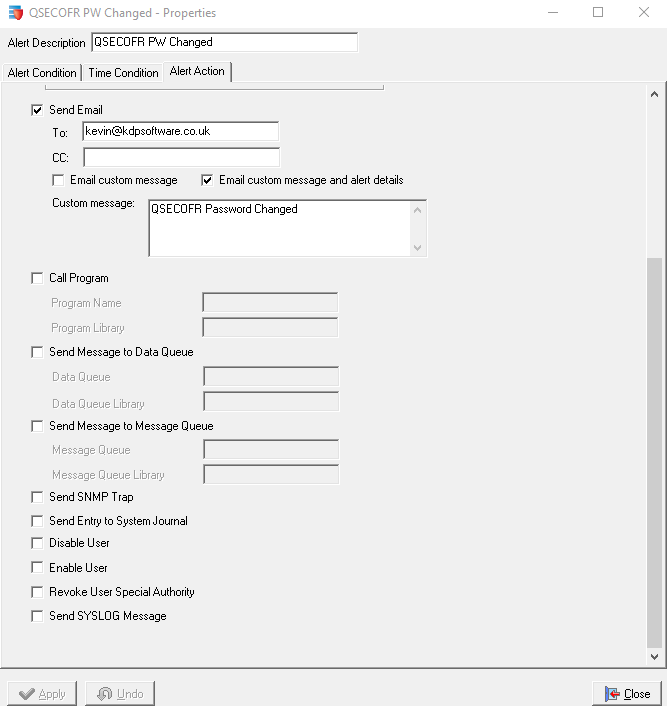
To extract events manually you need to use the command DSPAUDJRNE to extract the data to a file and then display that file. It's much easier to extract that information with a tool like Enforcive. You then have to perform the above actions manually once you have the report, Enforcive will perform these actions automatically and straight away.
For a free demonstration contact us using the Contact Page.



